Did you know that APIs are the backbone of modern applications, enabling seamless communication between services? Imagine the chaos if unauthorized users gained access to critical APIs. In this guide, we’ll explore how to secure your APIs effectively.
API security is paramount, especially in cloud environments like AWS. We’ll delve into best practices for enforcing access control. By the end of this post, you’ll have actionable strategies to safeguard your APIs and protect sensitive data.
Context
API security involves mechanisms to prevent unauthorized access, data breaches, and misuse. Because APIs power everything from mobile apps to microservices, their security directly impacts application integrity. Furthermore, with the rise of serverless architectures and distributed systems, understanding API security is more critical than ever.
Data Governance: The Cornerstone of Security
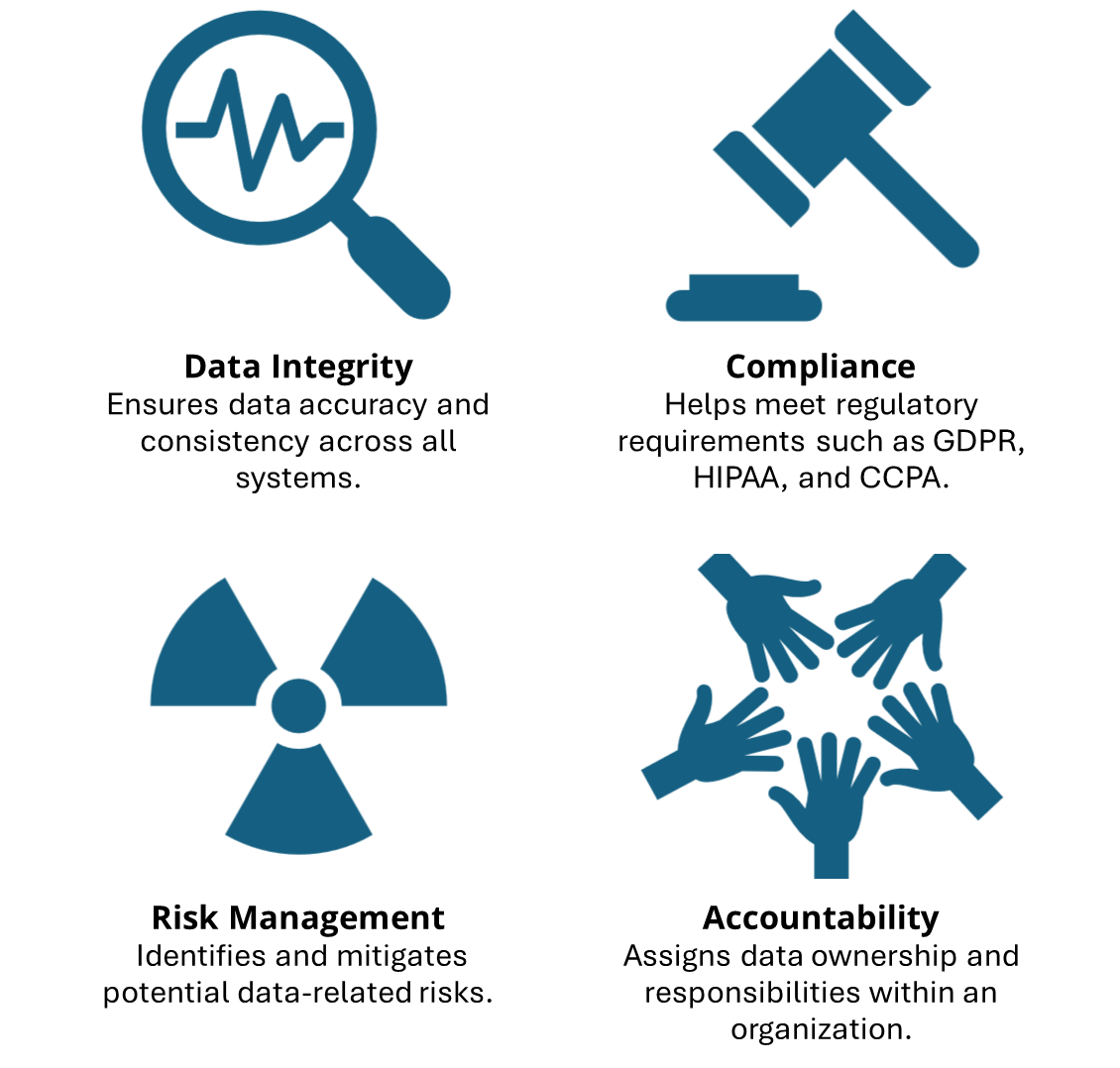
Data governance encompasses the policies, standards, and practices that ensure data is managed effectively throughout its lifecycle. In the context of API security, robust data governance is crucial. Here’s why:
The Imperative of Secure APIs
APIs are integral to modern business operations, connecting various systems, services, and applications. However, this interconnectedness also introduces security vulnerabilities. Here’s why securing your APIs is non-negotiable:
- Prevent Unauthorized Access: Protect sensitive data from being accessed by unauthorized users.
- Avoid Data Breaches: Secure APIs can prevent costly and damaging data breaches.
- Maintain Trust: Customers trust businesses that protect their data.
- Operational Continuity: Secure APIs ensure your services remain reliable and uninterrupted.
How Data Governance and Secure APIs Benefit Businesses
- Data Protection: Secure APIs help prevent unauthorized data leaks, protecting sensitive information such as customer details, financial records, and intellectual property.
- Regulatory Compliance: Proper data governance and API security ensure compliance with regulations, avoiding hefty fines and legal issues.
- Improved Decision Making: Accurate and secure data supports better business decisions.
- Enhanced Customer Trust: Demonstrating a commitment to data security builds customer confidence and loyalty.
How to Make This Possible with AWS
AWS offers a variety of services and tools to help you implement robust security for your APIs:
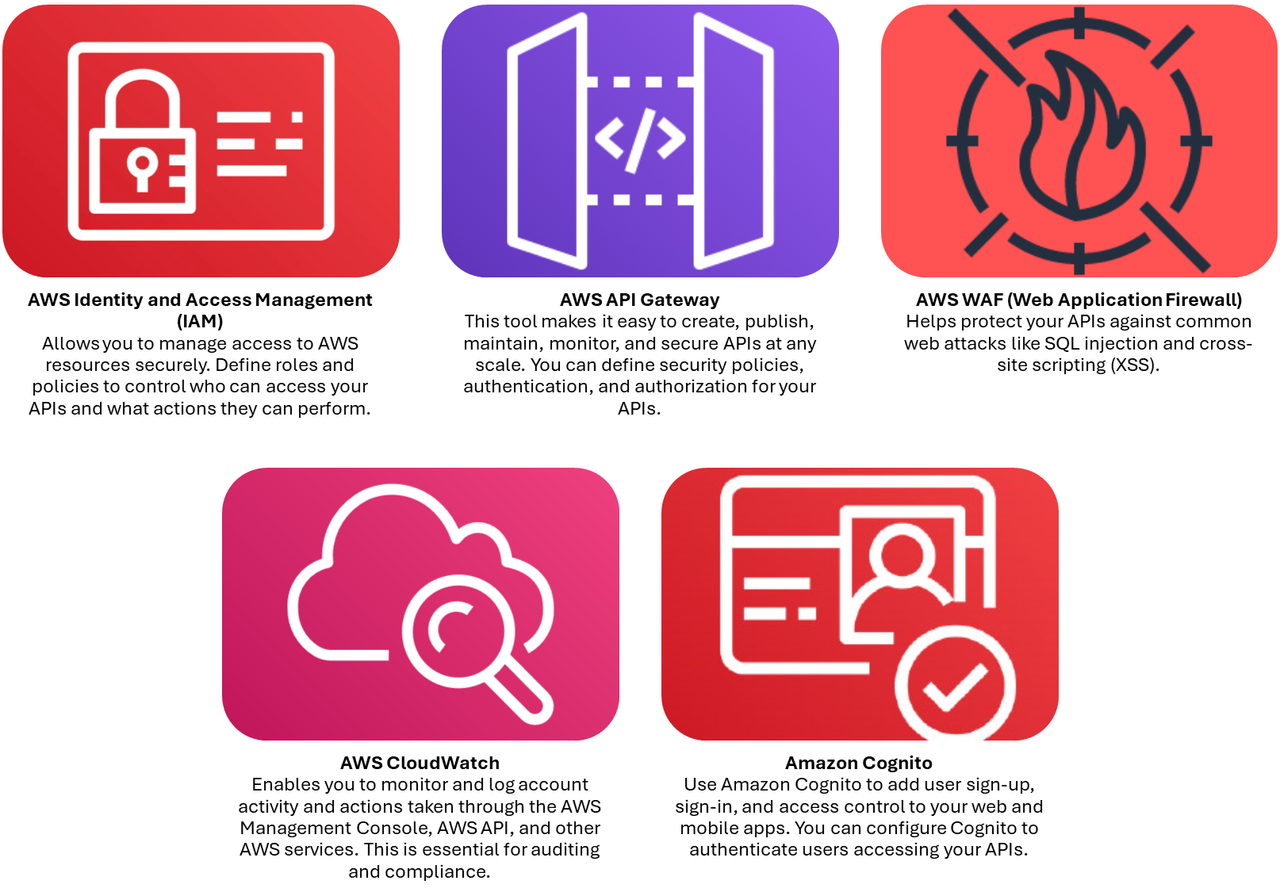
Types of Access in AWS and When to Use Them
In AWS, controlling access to your resources is crucial for ensuring security and compliance. Here are three types of access controls in AWS, along with examples of when and how to use them effectively:
1. AWS Cognito
What It Is: AWS Cognito is a service that provides user sign-up, sign-in, and access control to web and mobile apps. It allows you to manage user identities and authenticate users via social identity providers (such as Facebook, Google, and Amazon) or enterprise identity providers via SAML 2.0.
When to Use It: Use AWS Cognito when you need to manage user authentication and authorization for your applications, especially for mobile and web apps that require social login, user pools, or federated identities.
Example Use Case:
- Scenario: You are building a mobile app where users can sign up, log in, and access personalized content.
- Implementation: Use Cognito User Pools to handle user registration and authentication. Integrate social logins for convenience. Utilize Cognito Identity Pools to grant access to AWS resources based on the authenticated user’s role.
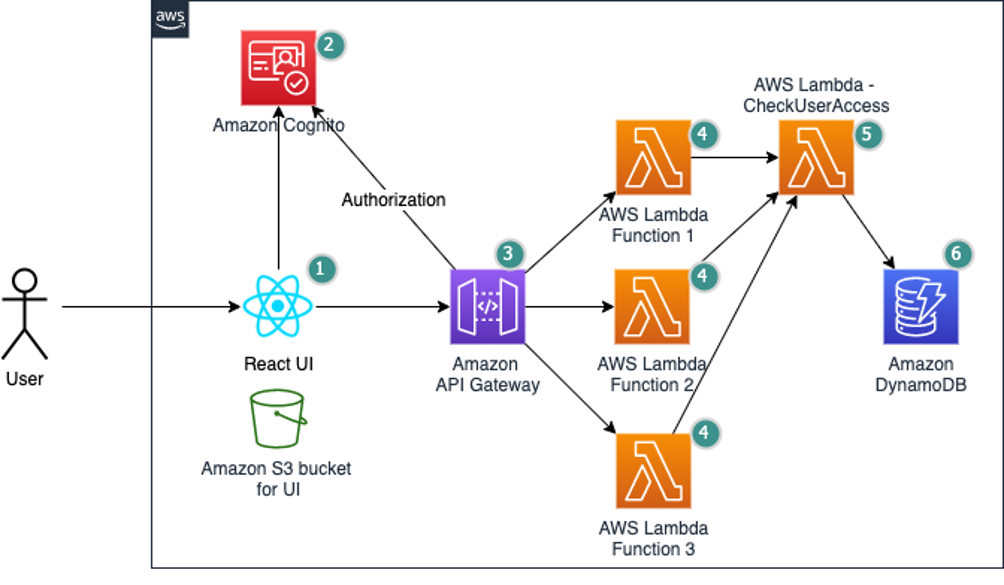
2. Custom Lambda Authorizer
What It Is: A custom Lambda authorizer (formerly known as a custom authorizer) is an AWS Lambda function that you create to control access to your APIs managed by API Gateway. This Lambda function is invoked to determine if a user should be allowed to invoke the API.
When to Use It: Use a custom Lambda authorizer when you need fine-grained access control or custom authentication logic that cannot be achieved using standard AWS IAM roles or policies.
Example Use Case:
- Scenario: You have an API that different clients access, and you need to implement custom authentication logic, such as validating a JWT token from a non-Cognito identity provider.
- Implementation: Create a Lambda function that verifies the token, extracts user roles, and returns an IAM policy granting or denying access to the API Gateway. Attach this Lambda authorizer to your API methods in API Gateway.
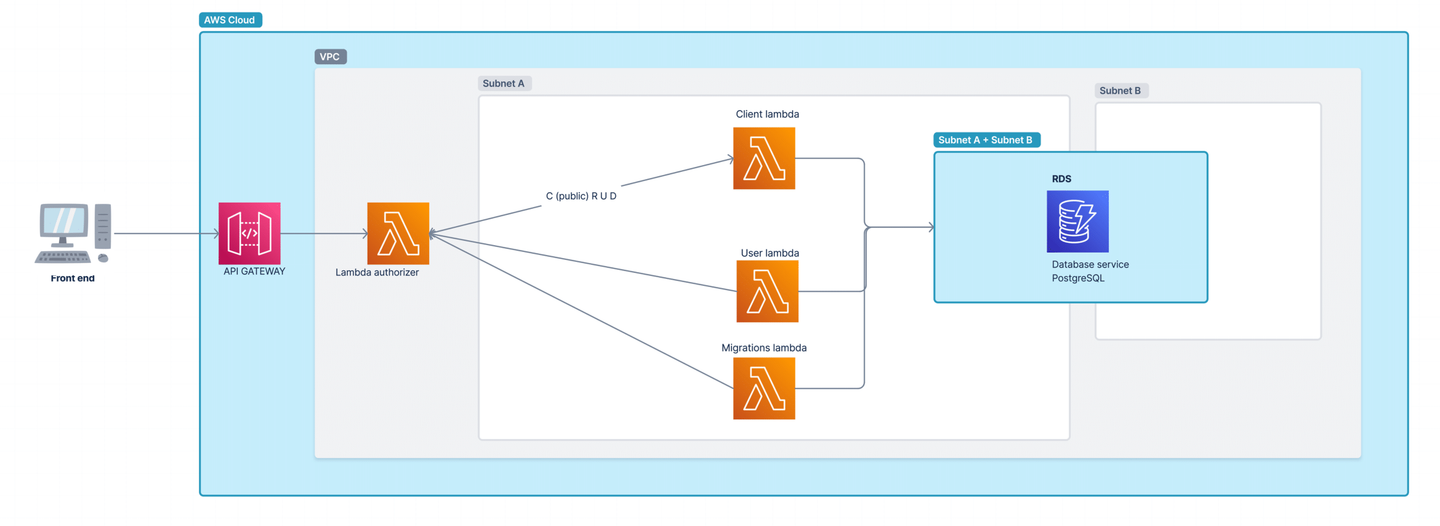
3. IAM Tags
What It Is: IAM tags are key-value pairs that you can attach to IAM entities (users, groups, roles, and policies). These tags can be used for attribute-based access control (ABAC) to manage permissions based on user attributes.
When to Use It: Use IAM tags when you need to manage access dynamically based on user attributes or when you want to implement ABAC for more flexible and scalable permission management.
Example
- Create IAM Policies for Each Role
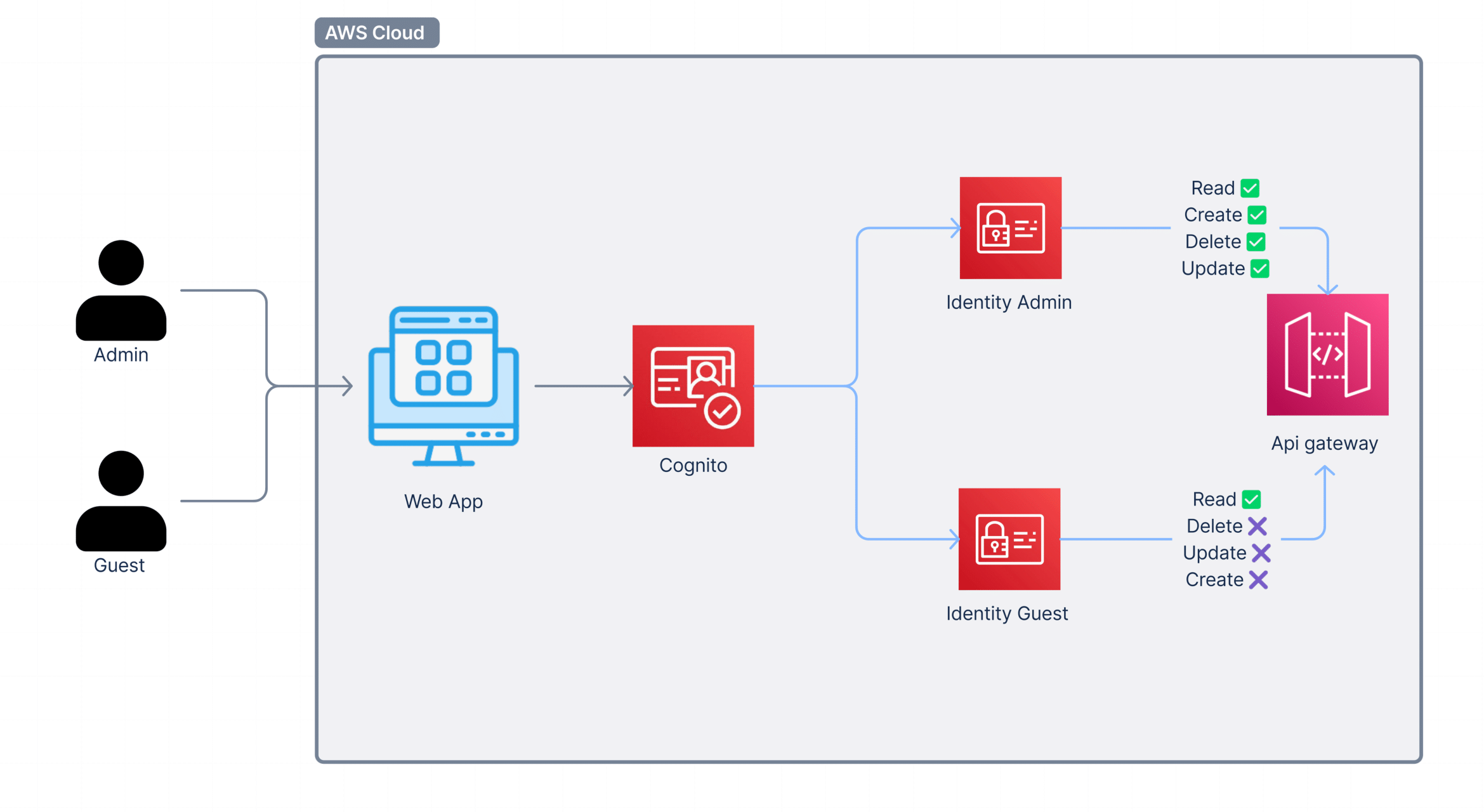
IAM policies are like rules that define what actions a user can perform. Let's break it down for non-technical readers:
- Admin Policy:
- What It Does: Allows the admin to perform any action (create, read, update, delete) on any part of the API.
- Why It’s Needed: Admins need full control to manage the system.
- Guest Policy:
- What It Does: Allows the guest to only read public information, without making any changes.
- Why It’s Needed: Guests should be able to access some information without compromising system security.
- Assign IAM Roles to Users
- Admin Role: Assign this role to users who need full administrative access to the API.
- Guest Role: Assign this role to users who only need access to public information.
- Configure API Gateway with IAM Roles
- Set Up API Gateway Resources and Methods:
- Create resources and methods (GET, POST, PUT, DELETE) in API Gateway.
- For admin methods (POST, PUT, DELETE), restrict access to users with the Admin role.
- For guest methods (GET), allow access to users with the Guest role.
- Apply IAM Role-Based Access Control:
- In the API Gateway settings, apply the IAM policies created for Admin and Guest roles.
- Use IAM roles and policies to enforce which users can invoke which API methods.
- Set Up API Gateway Resources and Methods:
Summary
By defining clear IAM roles and policies, and by using AWS tools such as IAM, API Gateway, and Cognito, you can ensure that your API remains secure and that users have the appropriate level of access based on their role. Admins can perform any actions, while guests have limited, read-only access to public data. This approach not only enhances security but also ensures operational efficiency and compliance with data governance standards.
Securing APIs prevents unauthorized data leaks, and proper access control ensures compliance with regulations such as GDPR and HIPAA.
Conclusion
Securing your APIs is essential to protect sensitive information, maintain operational continuity, and build user trust. By utilizing AWS tools like IAM, API Gateway, and Cognito, you can effectively manage roles and permissions, ensuring that only authorized users access specific data and functionalities. This approach not only enhances security but also supports compliance with regulations such as GDPR and HIPAA.
If you found this guide helpful, subscribe to our blog for more tips and insights on API security and other tech topics. Stay updated with the latest articles and join a community of professionals dedicated to advancing their knowledge and skills in the ever-evolving tech landscape. Don't miss out ✨ subscribe today!